A Catalyst forVerifiable Computing
The Intersection of
Distributed Systems &
Applied Cryptography
The Intersection of
Distributed Systems &
Applied Cryptography
We rely on digital systems in many important ways — from our finances, to our healthcare. As AI becomes pervasive, we will no longer be able to assume that systems are operating in a trustworthy manner. Rather, we will require systems to provide guarantees proving that they are free of manipulation, error, and malicious intent. Though nascent, the verifiable computing infrastructure that will deliver provable trust in digital processes is advancing rapidly.
HENCE is the first adaptive blockchain network. Its design introduces adaptive properties that enable it to evolve to meet the evolving needs of network participants. Although HENCE is a general-purpose infrastructure, its sole focus for the foreseeable future is on supporting the verifiable computing use cases sought by VCC members. These use cases are being realized through the development of specialized modules for executing verifiable computing tasks and delivering provable correctness across an diverse array of use cases.
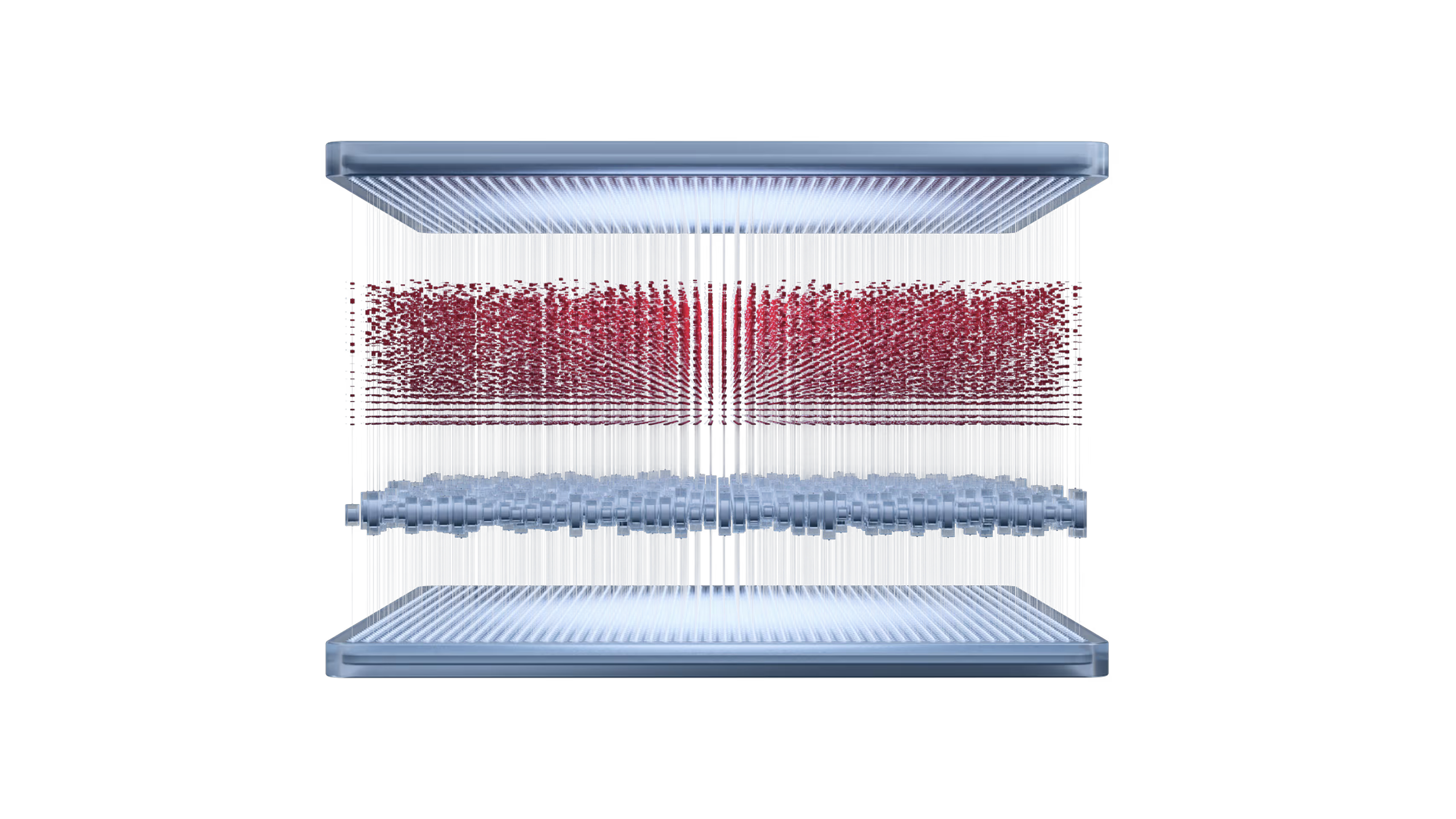
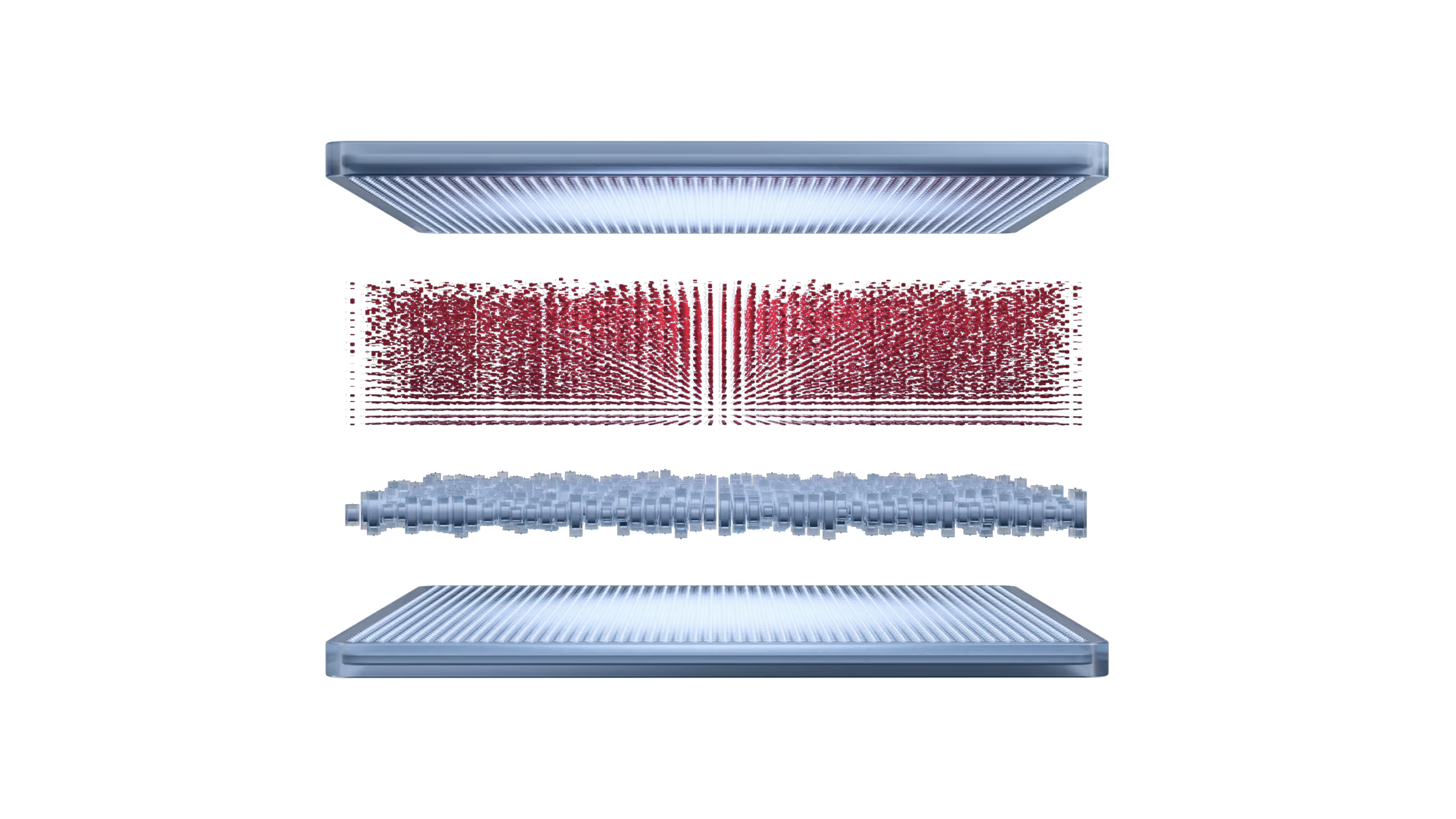
HENCE’s adaptation layer blockchain, the aChain, dynamically coordinates and provisions resources, automating eChain deployment for emerging industry- and use-case-specific needs, and routing user/agent requests to optimal specialized infrastructure within the HENCE ecosystem.
HENCE’s execution layer hosts specialized rollups called eChains. eChains are customizable according to industry- and use-case-specific requirements relating to execution environments, privacy schemes, schemes for integrating and interoperating with external IT systems, and more.
HENCE’s base layer blockchain, the mChain, guarantees neutrality, security, and final settlement for transactions executed on the network. It serves as a neutral foundation for AI-AI and AI-human interactions, and provides a lasting, tamper-proof record of events.
Automated Credit Decisions: Banks can prove that lending decisions adhere to fair-lending policies.
Fraud Detection: Financial institutions can prove that fraud detection algorithms operate without bias.
Algorithmic Trading Compliance: Trading firms can provide auditable proofs verifying compliant conduct.
Verifiable Clinical Trial Data: Organizations can prove data integrity for reliable trial outcomes.
Auditable Medical Records: Healthcare providers can prove patient health information accuracy.
Provenance for Pharmaceuticals: Companies can provide proofs verifying origin and custody chain.
Verifiable AI Model Integrity: Prove training data integrity and consistent, unbiased performance of AI outputs.
Auditable Data Storage: Verify data integrity against unauthorized changes; provide transparent access logs.
Transparent Content Provenance: Trace digital media origin and modification history to detect manipulation.
Verifiable Smart Meter Data: Prove accurate, untampered energy readings for fair billing practices.
Secure Control of Critical Infrastructure: Verify the integrity of operational commands.
Transparent Carbon Emissions Tracking: Provide auditable proof of emissions data for accurate reporting.
Verifiable E-commerce Transactions: Prove transaction details and secure fulfilment, reducing disputes.
Verifiable Product Provenance: Trace product origin, including ethical sourcing certifications.
Fair and Verifiable Loyalty Programs: Ensure accurate tracking and application of customer rewards.
Secure and Verifiable Voting Systems: Prove vote integrity and the accuracy of election tallies.
Tamper-Proof Digital Identity: Verify identity attributes securely for trusted online interactions.
Transparent and Auditable Public Records: Ensure record integrity and provide transparent access logs.
Verifiable Sensor Data: Prove accurate, untampered data for autonomous navigation and decisions.
Secure Over-the-Air Updates: Verify the authenticity and integrity of software updates.
Auditable Decision-Making Logs: Provide verifiable records of autonomous system actions.
Verifiable Quality Control: Prove product standards and the integrity of testing results.
Auditable Supply Chain Tracking: Verify component origin, transfer history, and condition.
Tamper-Proof Industrial Control Systems: Ensure the integrity of operational commands and configurations.
Verifiable Quality Control: Prove product standards and the integrity of testing results.
Auditable Supply Chain Tracking: Verify component origin, transfer history, and condition.
Tamper-Proof Industrial Control Systems: Ensure the integrity of operational commands and configurations.
Verifiable Property Ownership Records: Provide proof of ownership, title history, and transfer records.
Smart Contracts for Leasing: Ensure tamper-proof leases and automatically manage payments with verifiable logs.
Verifiable Building Information Models (BIM): Ensure the integrity and as-built accuracy of building models.
Dive deeper, and join us on Discord to engage in discussion with the HENCE community.
By subscribing, you consent to receive emails from HENCE